compromise assessment malaysia
Comply with industry regulations Avoid straining customer relationships as a results of breaches and leakage of sensitive data. OTP or one-time password refers to an alphanumeric or numeric code.

Compromise Assessment Ec Council Global Services Egs
With a typical end-to-end duration of approximately seven to nine.

. Malaysia through operations of branches and subsidiaries. 2 To identify the presence of any security breaches. Understanding when we are breached and resolving it should be the top priority.
Compromise Assessment is a high-level review of the security posture of an organization to identify if they are already compromised or breached. The compromised or not state of your environment your ability to identify vulnerabilities your ability to eliminate risks This is essential in running an effective SOC Security Operations Center. While penetration tests focus on finding vulnerabilities a compromise assessment focuses on whether an organization was breached without knowing it he explains.
Contact us for a free quotation today. In addition a compromise assessment can help highlight the risk associated with a compromise not being effectively communicated to seniorexecutive leadership within your organization. A body corporate which commits an offence under the Competition Act will attract a fine of up to Malaysian Ringgit RM 5 million while a second or subsequent offence will result in the imposition of a fine not exceeding RM 10 million.
Secure Software Development Lifecycle. Using Deloittes Cyber Compromise Assessment CCA on your estate will help identify if there is a current or indicators of a past compromise of your network - utilising the latest threat intelligence and detection techniques. Increasingly companies around the world understand that Compromise Assessments are a basic business imperative as they enable them to.
Compromise Assessment Malaysia LGMS 1 Cyber Security Provider 7 Who trust LGMS for professional cybersecurity services. The approach is designed to be light-touch with simple and temporary monitoring installations. He further explained that in Malaysia a compromised assessment is an exercise required by the local central bank to ensure the financial institutions FIs gain visibility to answer three basic questions.
They want to know if youre compromised can identify the compromise and if you can come up with an effective incident response strategy. Our Compromise Assessments are an essential business need for all organisations. 1 To comply with local laws regulations Eg.
Download Datasheet Demo To establish trust in the IT environment for the board and executives CyberStash conducts forensic-level analysis across the entire IT fleet at a. Compromise Assessment ServiceYour essential post-breach strategy for detecting systems already compromised by attacks that are too sophisticated for your existing security controls to catch. Our threat hunters will combine state-of-the-art targeted cyber threat intelligence network and endpoint detection to review your organizations infrastructure systems and applications in order to identify malware back-doors unauthorized access and indicators of compromise which could.
Bank Negara of Malaysias Risk Management in Technology. Vigilant Asia is an award-winning MSSP delivering compromise assessment services in Asia using ThreatDefence XDR platform. Material technology projects refers to projects which involve critical systems the delivery of essential services to customers or counterparties or compliance with regulatory requirements.
In an interview with Information. We are focused on identifying the cyber attacks that these first lines of defence may have missed. Compromise assessments CA answer the fundamental cyber security question Are we breached.
Our approach to Compromise Assessment The most sophisticated threat actors dedicate their time to finding ways of evading detection from traditional defence mechanisms such as antivirus. In an increasingly complex and dynamic threat landscape now more than ever organizations need to understand the effectiveness of. Compromise Assessment checks if any attacker activity or unauthorized access is already present in your network by analyzing data logs and existing telemetry to identify.
It takes organizations an average of 191 days to identify a data breach. Is Your IT Infrastructure Secured. Performing a compromise assessment gives you confidence in your awareness of.
Bank Negara Malaysia now encourages financial institutions to conduct a Compromise Assessment CA through a qualified professional service provider. Cybersecurity Posture and Maturity Assessment. Cyber Security Gap Analysis and Roadmap Development.
Usually there are a few reasons companies do a Compromise Assessment. Our CA service delivers a high-level review and audit of your organizations IT environment based on suspicious user behaviors logs compliances policies Indicators of Compromise IOCs or any evidence of malicious activities to identify attackers currently. Compromise Assessment Firmus 2020-06-14T1449110800.
Our compromise assessment service has been designed to answer that question.

Compromise Assessment 7 Things You Should Know Lgms Blog

Compromise Assessment Cybereason Assessments

Indicators Of Compromise Definition
What Is Compromise Assessment The Benefits How It S Different How By Cycraft Technology Corp Cycraft Medium

Compromise Assessment Condition Zebra Cyber Security Company Malaysia
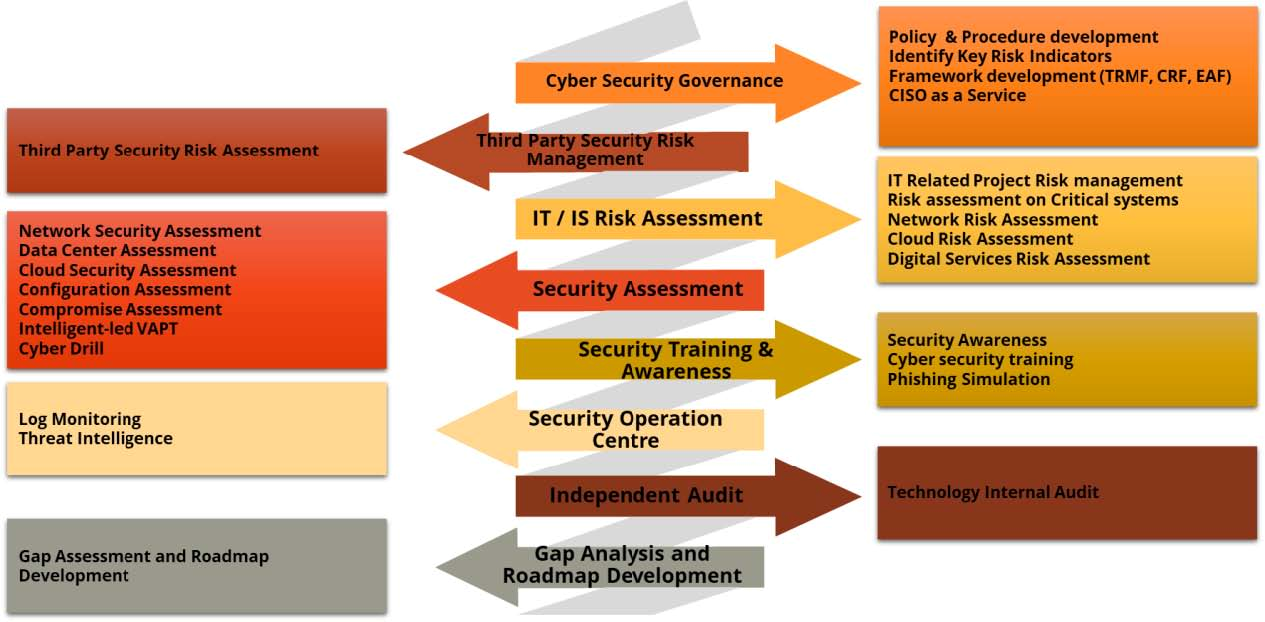
Risk Management In Technology Ec Council Global Services Egs

Cyber Compromise Assessment Deloitte China Risk Advisory

Technical Risk Assessment Data Sheet Crowdstrike

Compromise Assessment 7 Things You Should Know Lgms Blog
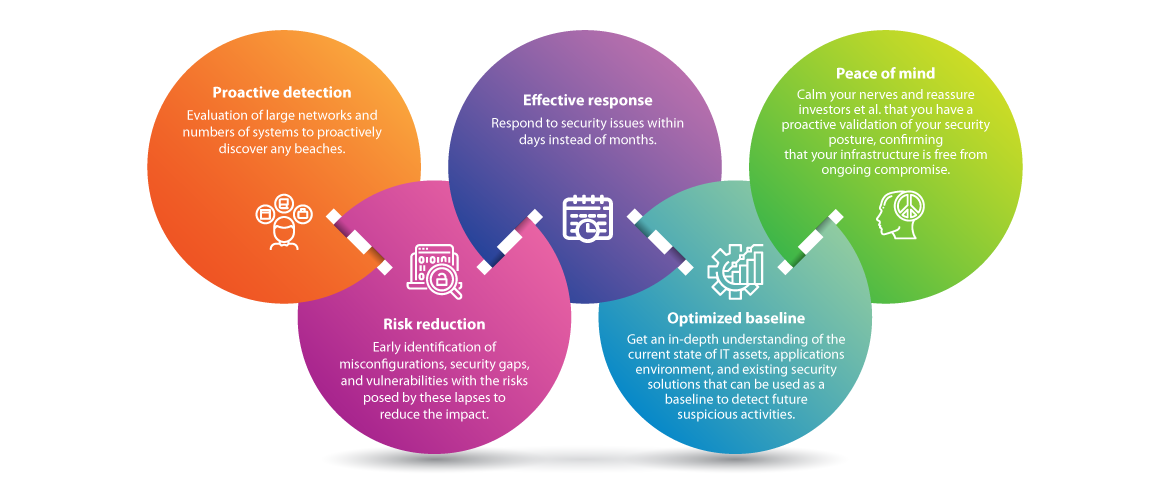
Compromise Assessment Ec Council Global Services Egs

Compromise Assessment Malaysia Uncover Hidden Security Risks Firmus

Compromise Assessment 7 Things You Should Know Lgms Blog

Compromise Assessment 7 Things You Should Know Lgms Blog

Compromise Assessment Condition Zebra Cyber Security Company Malaysia

Compromise Assessment 7 Things You Should Know Lgms Blog

Indicators Of Compromise Definition



0 Response to "compromise assessment malaysia"
Post a Comment